ISMG is a global authority, linking professionals and businesses with cutting-edge technology, AI, and cybersecurity advancements via industry-leading news, research, dynamic events, strategic education, and specialized marketing services.
Our Brands

1.6M+
Subscribers
38
Media Properties

Media Network
ISMG's editorial brands deliver cutting-edge news, insights, and
analysis in cybersecurity and technology, engaging over 1.6
million subscribers globally with quality journalism and thought
leadership.

400+
Global Annual Events
20,000+
Attendees Annually

Global Events
Connecting industry leaders through education and networking,
ISMG's global events include summits, roundtables, and custom
events, designed to foster collaboration and innovation in tech
and security.

500+
Custom Learning Paths
30+
Custom Learning Paths

Through practical, real-world training, CyberEd.io bridges the cybersecurity skills gap, offering custom-designed learning paths from entry-level to CISO, curated by industry experts.

2K+
Members
91%
Attendees Annually
85+
Industries
75+
Countries


The exclusive CyberEdBoard community offers CISOs and CIOs a
platform for executive-level education and peer-to-peer
knowledge sharing, addressing today’s challenges in security and
IT.



CyberTheory advises cybersecurity firms with data-driven
marketing strategies, leveraging insider intelligence and
proprietary data models to optimize marketing outcomes.
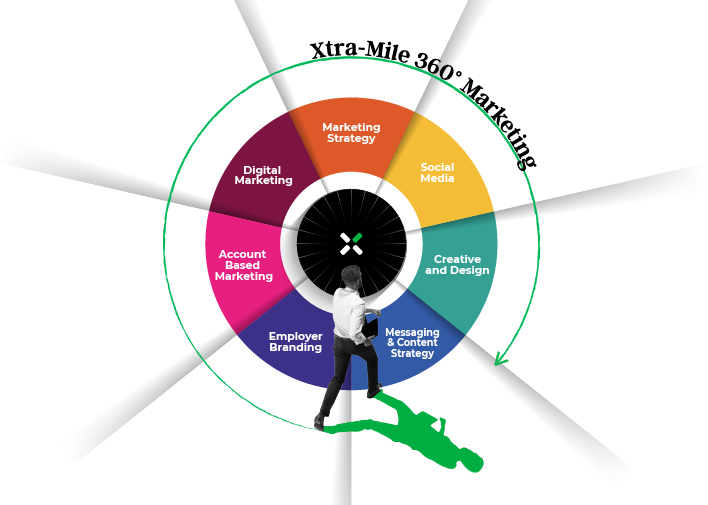

Specializing in lifecycle marketing, XtraMile drives results
from engagement to retention, enhancing employer branding and
customer relationships with end-to-end marketing solutions.



CIO.inc focuses on the intersection of business and IT,
providing CIOs and tech executives with critical insights,
strategies, and thought leadership to navigate the digital
landscape.


Athena offers actionable, contact-level buyer intent insights
based on proprietary data, giving marketers and sellers a
competitive edge in targeting and communication.
